Cuckoo is a free malware analysis system. You can analyze any suspicious file with Cuckoo and it will give you some very detailed feedback:
- Traffic captures in Pcap format.
- Traces of win32 API calls.
- Information about processes created by the malware.
- Files that have been downloaded, modified or removed during the malware execution.
- Register keys that have been modified.
- Malware behavior.
- Screenshots taken while the malware was running.
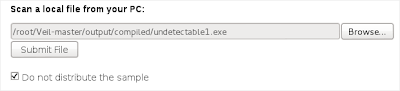
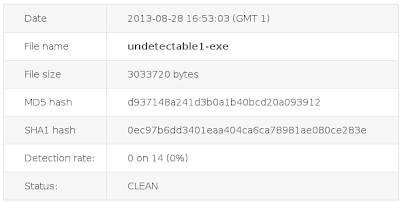
You can use this website if you want to test it for free.
https://malwr.com/In this post I'm going to show you how to install your own Cuckoo for the purpose of malware investigation.
My computer has the following operating system.
lsb_release -a
No LSB modules are available
Distributor ID: Ubuntu
Description: Ubuntu 10.04.3 LTS
Release: 10.04
Codename: lucid
It is necessary to install SQLAlchemy for Cuckoo.
apt-get install python-sqlalchemy
There are other optional dependencies. Their installation is recommended:
- Dpkt (Highly Recommended): for extracting relevant information from PCAP files.
- Jinja2 (Highly Recommended): for rendering the HTML reports and the web interface.
- Magic (Optional): for identifying files’ formats (otherwise use “file” command line utility)
- Pydeep (Optional): for calculating ssdeep fuzzy hash of files.
- Pymongo (Optional): for storing the results in a MongoDB database.
- Yara and Yara Python (Optional): for matching Yara signatures (use the svn version).
- Libvirt (Optional): for using the KVM machine manager.
- Bottlepy (Optional): for using the web.py and api.py utilities.
- Pefile (Optional): used for static analysis of PE32 binaries.
We can Install the majority of them through the Debian repositories.
apt-get install python-dpkt python-jinja2 python-magic python-libvirt python-bottle python-pefile
We can install pymongo with pip
apt-get install python-pip
pip install pymongo
Now, we are going to download and install Yara.
apt-get install libpcre3 libpcre3-dev
wget http://yara-project.googlecode.com/files/yara-1.7.tar.gz
wget http://yara-project.googlecode.com/files/yara-python-1.7.tar.gz
tar xvfz yara-1.7.tar.gz
cd yara-1.7
./configure
make
make check
cd ..
tar xvfz yara-python-1.7.tar.gz
cd yara-python-1.7
python setup.py build
python setup.py install
It's a requirement to have installed Ssdeep before installing Pydeep. We can download it from:
http://sourceforge.net/projects/ssdeep/files/ssdeep-2.10/ssdeep-2.10.tar.gz/downloadThen, we are going to install it.
tar xvfz ssdeep-2.10.tar.gz
cd ssdeep-2.10
./configure
make
make check
make install
Now, we are going to download and install Pydeep
wget https://github.com/kbandla/pydeep/archive/master.zip
unzip master.zip
cd pydeep-master
python setup.py build
sudo python setup.py install
If you haven't installed Tcpdump yet, you need to install it. With the following commands we can run Tcpdump as a normal user instead of a root user.
apt-get install tcpdump
chmod +s /usr/sbin/tcpdump
apt-get install libcap2-bin
setcap cap_net_raw,cap_net_admin=eip /usr/sbin/tcpdump
getcap /usr/sbin/tcpdump
apt-get install libcap2-bin
setcap cap_net_raw,cap_net_admin=eip /usr/sbin/tcpdump
getcap /usr/sbin/tcpdump
Currently we have all the Cuckoo's tools installed. Now we need to install Virtualbox in order to create our Windows Virtual machine where we will run the malware. Remember when you are installing the Windows operating system to disable the automatic updates and install the old software versions like Adobe Reader, Java, Flash Player. We want to have a vulnerable virtual machine.
wget http://download.virtualbox.org/virtualbox/4.2.16/virtualbox-4.2_4.2.16-86992~Ubuntu~lucid_i386.deb
dpkg -i virtualbox-4.2_4.2.16-86992~Ubuntu~lucid_i386.deb
Now, we are going to create a cuckoo user with permission from the Virtualbox machines.
adduser cuckoo
usermod -G vboxusers cuckoo
We should download Cuckoo from the original repository.
wget https://github.com/cuckoobox/cuckoo/archive/master.zip
unzip master.zip
cd cuckoo-master/
It's necesary to have the following tools installed on the Windows Virtual Machine.
The next step is to copy the Cuckoo agent.py from the Cuckoo package to the virtual machine. Then it's necessary to excute it. If you want, you can create a key register allowing the agent to run automatically each time the computer is restarted.
Now, we need to change the following settings on the Cuckoo Server.
This is my configuration of the Virtual machine.
virtualbox.conf
mode = headless
path = /usr/bin/VBoxManage
machines = Cuckoo Sandbox
label = Cuckoo Sandbox
platform = windows
ip = 192.168.56.101
This is my configuration of the cuckoo server.
cuckoo.conf
[cuckoo]
version_check = on
delete_original = off
machine_manager = virtualbox
[resultserver]
ip = 192.168.56.1
port = 2042
interface = vboxnet0
Configuring the Virtualbox server this way is necessary in order to get the traffic capture with tcpdump.
vboxmanage hostonlyif create
vboxmanage hostonlyif ipconfig vboxnet0 --ip 192.168.56.1
vboxmanage modifyvm 'Cuckoo Sandbox' --hostonlyadapter1 vboxnet0
vboxmanage modifyvm 'Cuckoo Sandbox' --nic1 hostonly
We need to configure these network settings on the virtual machine.
Static IP - 192.168.56.101
DNS - any DNS server (8.8.8.8)
Default Gateway - 192.168.56.1
Now, we need to forward the packets through the server:
sudo iptables -A FORWARD -o eth0 -i vboxnet0 -s 192.168.56.0/24 -m conntrack --ctstate NEW -j ACCEPT
sudo iptables -A FORWARD -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
sudo iptables -A POSTROUTING -t nat -j MASQUERADE
sudo echo 1 > /proc/sys/net/ipv4/ip_forward or sudo sysctl -w net.ipv4.ip_forward=1
When you have everything ready, you need to take a screenshot of your Virtual Machine.
vboxmanage snapshot "Cuckoo Sandbox" take "Cuckoo Sandbox" --pause
The first time I ran Cuckoo, I had a problem that I fixed with the following command.
pip install argparse
Now we are going to play with malware files. First of all, we need to run the Cuckoo server.
jnieto@behindthefirewalls:~/cuckoo/cuckoo-master$ python cuckoo.py
We are going to send a malware file to the virtual machine and we are going to wait a moment while the malware is running and Cuckoo is analyzing it...
python submit.py /home/jnieto/cuckoo/cuckoo-master/malware_samples/iwmsax.exe
When the analysis is finished, we can see all these files.
We can see the HTML report and view all the information about the malware.
When we have finished testing the malware, we need to recover the fresh screenshot of our operating system again. We are going to use the following commands.
vboxmanage controlvm "Cuckoo Sandbox" poweroff
vboxmanage snapshot "Cuckoo Sandbox" restorecurrent
vboxheadless --startvm "Cuckoo Sandbox"
References:
Santi's LabsPrecisionsecCuckoosandboxVirtualboxVirustotal






























































































































_11.24.12.png)











